Today, CrowdStrike is releasing automated baseline enforcement and remediation in CrowdStrike Falcon® for IT to secure misconfigured devices and consistently address vulnerabilities across endpoints. Operators can now centrally manage and enforce endpoint configurations across platforms to support security and compliance efforts.
Security and IT teams must ensure endpoints are secure and compliant according to established baseline configurations, even as users install or remove apps, delay updates, or change settings. In addition, these teams must identify and quickly remediate security vulnerabilities for all devices. Resolving these issues requires deep endpoint visibility and coordinated response actions, which have long been siloed between security and IT.
Falcon for IT breaks down these silos to resolve issues before adversaries can exploit them. Our technology unifies visibility and enforcement within the CrowdStrike Falcon® cybersecurity platform to streamline operations and ensure security gaps are addressed.
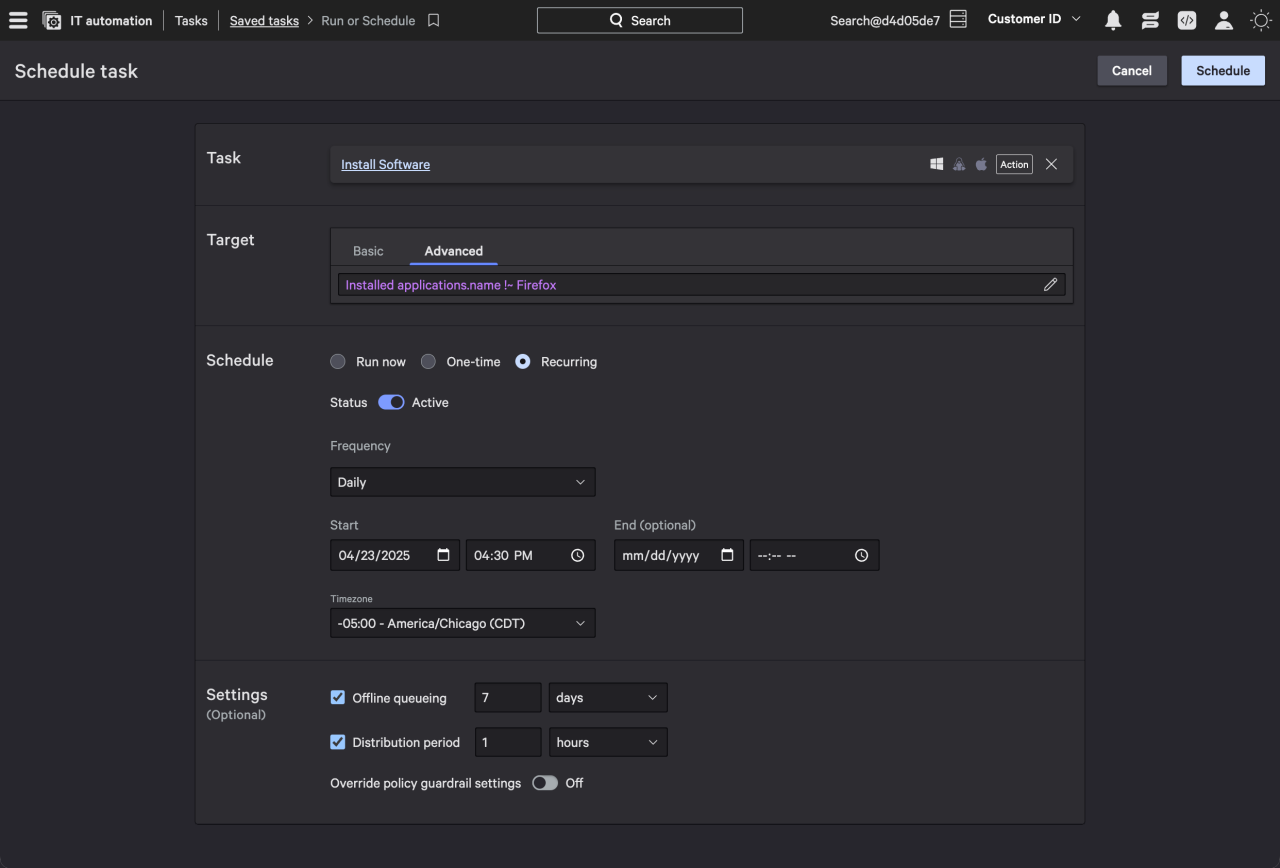
Building on Falcon for IT’s comprehensive visibility, our new baseline enforcement and automated remediation capabilities empower teams to quickly correct misconfigurations and vulnerabilities at scale — transforming manual tasks into proactive protection.
Intelligent Endpoint Automation Maintains Secure Endpoint Baselines
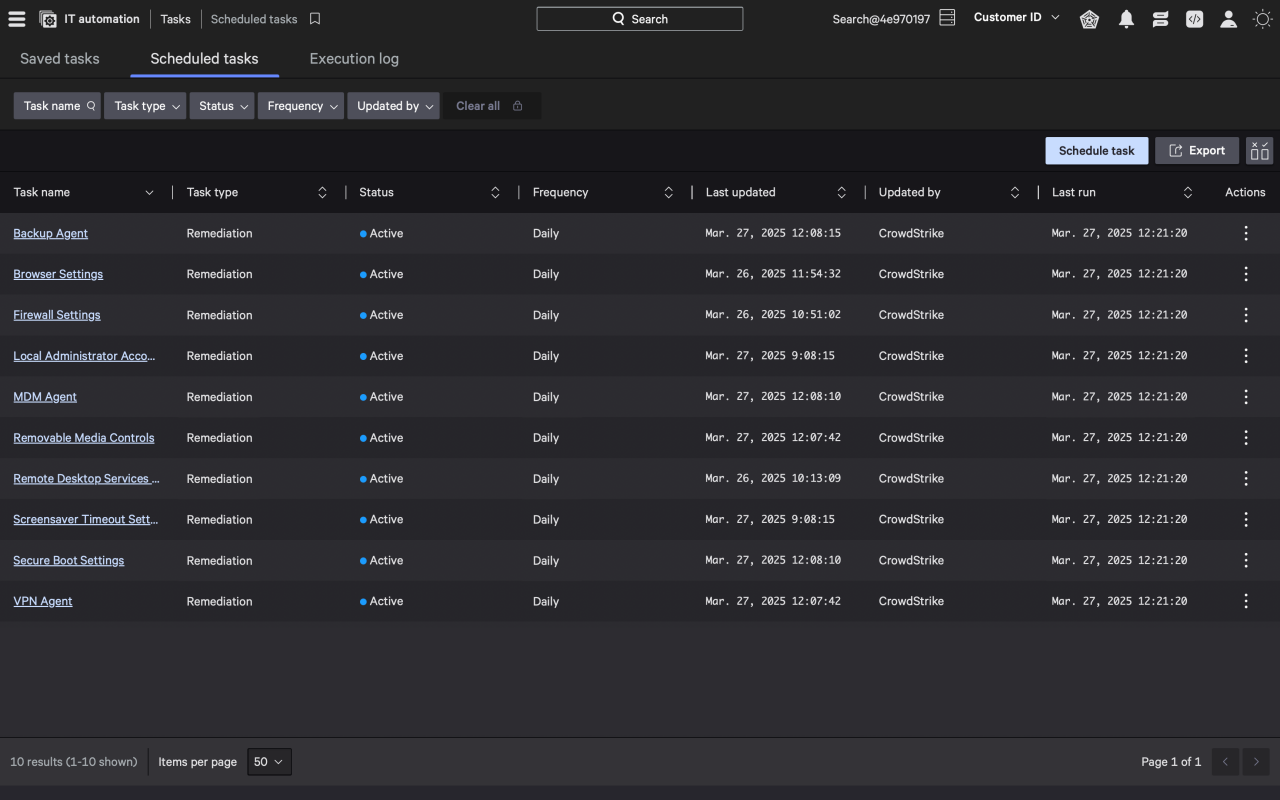
Falcon for IT now enables SecOps teams to define and enforce a desired endpoint state, whether that involves approved software, essential configurations, or required services. It continuously monitors for drift and automatically remediates deviations, simplifying critical maintenance for security and IT teams.
One of the biggest challenges in securing endpoints is the lack of full visibility across all devices. To make matters worse, security and IT teams often operate separately and use different tools to spot and fix problems. Relying on manual processes to detect and correct misconfigurations is both time-consuming and prone to error, leading to security gaps and compliance issues.
This new automation eliminates manual workflows while ensuring endpoints remain aligned to organizational policies and security benchmarks such as CIS, NIST, and DISA STIGs. By taking a unified approach to risk reduction and posture management with the Falcon platform, security teams can more effectively manage endpoint security and compliance across the enterprise.
Intelligent endpoint automation enables:
- Consistent configuration management across Windows, macOS, and Linux
- Scalable remediation for non-compliant systems
- Continuous alignment with frameworks like CIS, NIST, and DISA to reduce risk and support audit readiness





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)