CrowdStrike is excited to announce CrowdStrike Falcon Privileged Access, a new offering within CrowdStrike Falcon® Identity Protection that uses high-fidelity risk signals to provide just-in-time access to organizations’ critical permissions and resources.
Adversaries know valid credentials unlock access to data, infrastructure, and capabilities. Nearly 80% of attacks to gain initial access are malware-free, the CrowdStrike 2025 Global Threat Report found, indicating threat actors are using trusted identities and other alternative methods to infiltrate organizations undetected. Access broker advertisements, often selling valid credentials, were up 50% between 2023 and 2024.
The more privileged those credentials are, the more value they have. Accounts with elevated permissions and capabilities allow users to access sensitive data, perform administrative tasks, and make system-wide changes that other users can’t. SCATTERED SPIDER is one adversary using stolen credentials and social engineering to gain unauthorized account access. FAMOUS CHOLLIMA embeds malicious insiders in target organizations and works to escalate privileges.
Today, we are extending the power of CrowdStrike Falcon Identity Protection with Falcon Privileged Access, as well as unifying identity security and next-gen SIEM, and delivering agentic AI-driven detection triage for identity-based attacks.
Inside Falcon Privileged Access
Falcon Privileged Access, a new offering in Falcon Identity Protection, uses just-in-time access rather than the “standing privilege” method of traditional PAM solutions. It ensures users only receive elevated permissions for what they need, when they need it, as security policies allow.
Built into the unified CrowdStrike Falcon® cybersecurity platform, Falcon Privileged Access uses real-time signals from endpoints/devices, industry-leading threat intelligence, and advanced AI trained on trillions of security events to analyze user behavior and privilege status, and dynamically grant, block, or revoke access. Privileged access is only granted when security conditions are met, without manual approvals or workflow disruptions. Real-time risk signals from the Falcon platform continuously assess user and device context. If risk conditions change, privileges are revoked, and users can be forced to reauthenticate.
Falcon Privileged Access, now generally available, will provide seamless hybrid privileged access across on-premises Active Directory and cloud identity providers, including Microsoft Entra ID, without infrastructure changes or separate access request portals. Just-in-time access complements broader PAM capabilities — including password vaulting and session recording — by delivering real-time visibility and dynamic policy enforcement from a unified platform that secures the identity attack lifecycle.
With just-in-time enforcement, continuous authentication, and real-time risk-based controls, Falcon Privileged Access extends the power of Falcon Identity Protection and empowers organizations to reduce their identity attack surface across hybrid environments.
Falcon Identity Protection + Falcon Next-Gen SIEM
CrowdStrike is integrating Falcon Identity Protection and CrowdStrike Falcon® Next-Gen SIEM to empower security teams with automation to improve efficiency, reduce false positives, and more effectively detect and prioritize identity-based threats. This integration is now generally available to customers of both modules.
As part of the integration, CrowdStrike Falcon® Fusion SOAR — which is integrated with Falcon Next-Gen SIEM — allows security teams to automate Active Directory response actions without relying on identity and access management (IAM) teams. These actions may include, for example, disabling compromised accounts or adjusting user groups.
Falcon Fusion SOAR can also automatically enforce multifactor authentication (MFA) according to customer needs. For example, if an organization wants to require MFA for every login of a specific application, they can adjust Falcon Fusion SOAR to automate that requirement. This reduces the risk of false positives while strengthening security and adhering to business needs.
The integration of Falcon Identity Protection and Falcon Next-Gen SIEM accelerates investigations with advanced behavioral analytics, automated response, and identity-driven context. Security teams can detect compromised privileged users, automate Active Directory actions, and enforce MFA policies in real time — quickly turning signals into action.
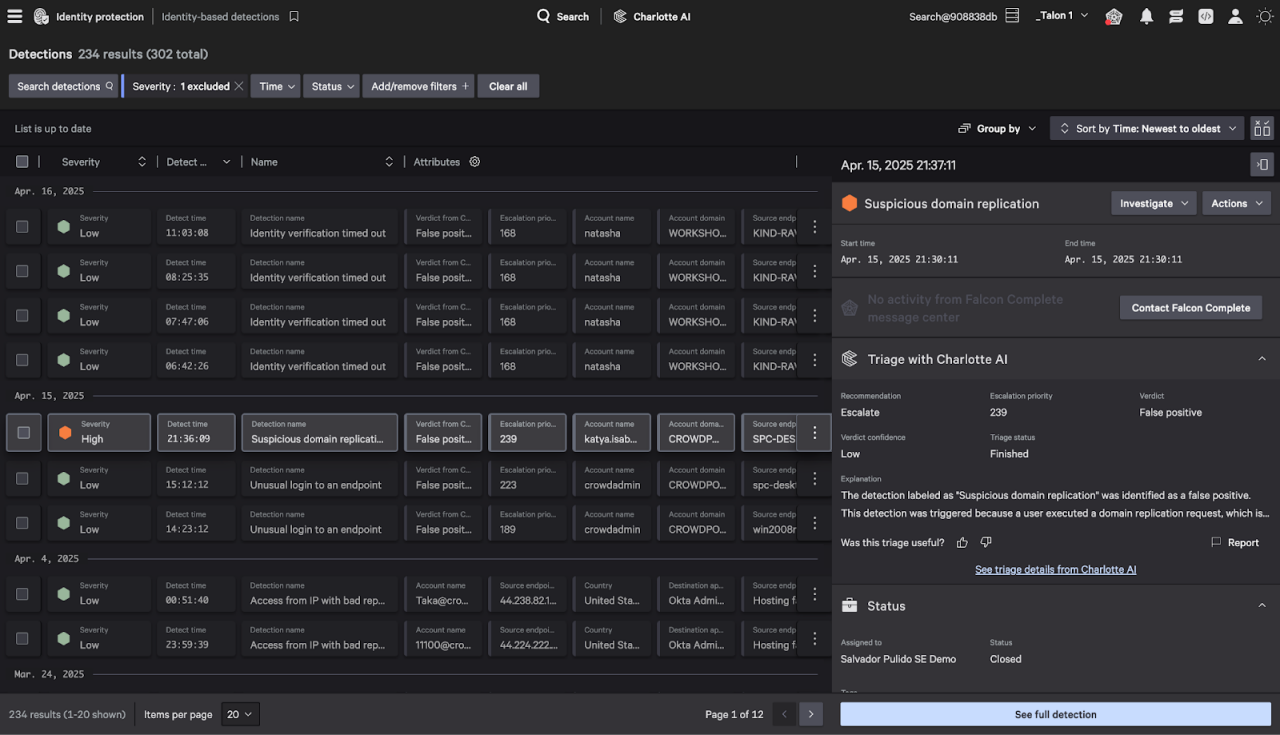
Charlotte AI Detection Triage Tackles Identity-Based Threats
CrowdStrike Charlotte AI™ Detection Triage now autonomously triages identity-based attacks, tackling one of modern security operations’ most persistent challenges: the manual, time-consuming effort required to analyze detections. Trained on millions of real-world SOC decisions from CrowdStrike Falcon® Complete Next-Gen MDR, this agentic AI capability delivers expert-level triage — automating work that typically consumes dozens, if not hundreds, of analyst hours per week.
With Charlotte AI, security teams can slash alert fatigue, eliminate false positives, and quickly surface the threats that matter most, whether they originate from a compromised identity or an endpoint. The result: faster response, fewer manual hours, and decisive clarity across even the most complex, cross-domain attacks — all at no additional cost to Charlotte AI customers.





![Helping Non-Security Stakeholders Understand ATT&CK in 10 Minutes or Less [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/video-ATTCK2-1)
![Qatar’s Commercial Bank Chooses CrowdStrike Falcon®: A Partnership Based on Trust [VIDEO]](https://assets.crowdstrike.com/is/image/crowdstrikeinc/Edward-Gonam-Qatar-Blog2-1)